While completely practical (and probably wise), there’s something a bit sad about the fact that Barack Obama will more or less be forced to give up e-mail access upon his ascension to the Presidency. E-mail communication has, in many ways, completely supplanted telephone communication in the 21st century; to me, this would be like telling any of the 20th century Presidents that they had to give up the phones on their desks. It seems like there must be a way to figure this one out…
I frequently find myself attached to some public wifi hotspot trying to get work done, and while I try to make most of my connections via secure methods (e.g., all my email takes place over encrypted connections), most of my web surfing takes place in cleartext. Occasionally, I’ll read some weblog post about the various hosted VPN services and think that I should just use one of them, but never really get around to it. This week, I finally bit the bullet… but rather than subscribing to one of the services, I just set up my own VPN server at home to use.
I have a Linux machine in my home network, and I flirted with the idea of installing OpenVPN on it and using that as my server, but due to a few weird complexities in where that machine sits on my network, that wasn’t the most appetizing idea to me. It was then that I wondered whether someone had built a VMware virtual appliance with OpenVPN support, and it turns out that PhoneHome was just the ticket I was looking for. On my home Windows 2003 Server box, I started that puppy up in VMware Player; it took about a half-hour’s worth of tweaking to get it set up just perfectly for me, and another half-hour to get my home firewall (well, really a Cisco router with a detailed set of access rules) set up to play nicely with the server. Now, I have an easy-to-run, easy-to-connect-to VPN server that allows me to have a secure connection no matter where I am, and that just rocks.
One of the things I was worried about was that the VPN would massively slow down my network connection; between the bottleneck of encrypting all the tunneled traffic and the bottleneck of my home internet connection, I was pretty sure I’d be less than impressed with the speed of an always-on VPN. Surprisingly, the connection is pretty damn fast, though — I appear to have the full speed of my home T1 available to me.
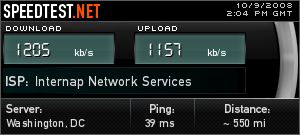
If anyone’s interested, I’m happy to share details of the changes I made to the PhoneHome VMware appliance, and any other info you might want.
So if you’re even tangentially exposed to news about the internet (or listen to NPR’s All Things Considered!), you might have heard about a major, major weakness that was discovered not too long ago in the security behind the way that hostnames are turned into IP addresses, a weakness that could easily lead to all kinds of hacks, exploitations, and general insecurity on the ‘net. Most of the folks responsible for the DNS servers — the bits of software that are affected by this — were quickly briefed about the flaw and given a chance to respond, and nearly all of them just as quickly released patches to their software to make the hacks much harder to accomplish. Apple was certainly part of the former group (having been briefed on May 5th), but was not part of the latter group; by July 8th, all other operating system vendors had patched the vulnerability, while it took Apple until July 31st to roll the patch out the door. And within a few days, folks were noticing that Apple’s patch only handled half of the issue, remedying Mac servers while ignoring Mac client (i.e., desktop) machines.
Interested in which other Apple platforms were both affected by the DNS flaw and unpatched, I did a little playing with my Airport Extreme wifi router today — I figured it was a good platform to test, seeing as the way it fits into the environment that surrounds this particular DNS flaw is more as a server (a device being asked to resolve DNS names) than as a client (a device doing the asking). Additionally, there’s currently a lot of concern that even with all the patches released over the past month, it’s exactly devices like these — home routers that do DNS resolution alongside network address translation — that are going to prove the hardest to secure. Fortunately, after doing a bit of network sniffing, I can report that the Airport Extreme currently does exhibit patched behavior, properly choosing random ports from which to send its DNS queries. (And thus, that ISS post I linked to isn’t exactly correct when it says that no NAT vendor is performing source port randomization — clearly, Apple is doing the right thing when it comes to the Airport Extreme.)
The whole techie-bringing-San-Fran-to-its-knees story keeps getting better and better — it turns out that the passwords that Terry Childs gave to San Francisco mayor Gavin Newsom only allowed access to the network from a single hidden computer in the Hall of Justice. Better still, Childs locked well over a thousand modems in filing cabinets throughout various city agencies, all of which are connected to the system and which might be capable of allowing him (or others) access to the network to wreak more havoc. Was anyone overseeing the design and implementation of this network?
One of my favorite stories over the past week has been San Francisco losing control of its agency-wide network (SkyNet, anyone?) to a “rogue” employee who had designed the system and then locked everyone but himself out of administering it. The whole thing smacks of a bad plot for the next Die Hard movie (“Die Harderest, where Bruce Willis has to interrupt his shuffleboard game to save the Transamerica Building!”), or at least of the third installment of the Camel Club. Well, alas, the drama is over — yesterday, Mayor Gavin Newsom visited the employee’s holding cell and was able to coax the administrative login information out of him, and now the city is understandably going to look into how one lone person was able to singlehandedly control the pipes through which the majority of San Francisco’s inter-agency traffic flows.
For those who are all excited about Twitabit, the service that promises to queue up Twitter postings if the service is down, consider these two factlets:
- Twitabit asks you to type in your Twitter password — as in, you’re on a page on twitabit.com and asked to type in your password to another site entirely;
- Twitabit appears to have not one word of a privacy policy, or any other text that’ll help you understand why on Earth you should trust them with your password to another site.
Ummmm, no thanks. No thanks at all.
Hallelujah, the SuperDuper update to bring Leopard compatibility is now out! (For those who don’t know what the hell I’m talking about, or who might know and don’t use it, SuperDuper is by far the best backup app for Macs. And since Leopard, the latest version of Mac OS X, was released, SuperDuper didn’t work with it, leaving some of us without our backup method of choice.)
Ok, without a doubt, Shannon and I clearly will need to be buying this book as soon as it becomes available on Amazon.

In part inspired by Anil’s recent series of unsolicited testimonials, and in part as a result of receiving some really interesting gifts this holiday season, I’ve decided to try to get my shit together enough to post a few short unsolicited reviews over the next few days. (Note that these are reviews, and not necessarily testimonials, since at least one of them ain’t gonna be all that glowing.) And that leads to part one, my review of the Eye-Fi wireless memory card.
First, I should explain what the Eye-Fi is (since telling my family about it over the past few days taught me that this puppy is amazing enough to defy belief for some people). Simply put, the Eye-Fi is a 2 gigabyte memory card for your camera that has a wireless network adapter built into it. (Specifically, it’s a Secure Digital, or SD, card.) You use the card the same way you’d use any memory card in your camera; when you shoot your photos, they’re stored on the card, nothing special there. What is special is that after you take your photos, the card uses its built-in wireless capabilities to send the photos you take to your computer and any of a number of online photo sharing services, all automatically. Seriously, people — it’s like magic, all for the paltry price of $99 at Amazon.
So, now that that’s out of the way, let’s look at the user experience from the moment of unwrapping. The Eye-Fi box itself is pretty clever, with a little pull-tab on the right that causes the left side of the box to slide open and reveal the card and its USB adapter. Starting to use the Eye-Fi involves plugging the card into the USB adapter, plugging the adapter into any USB port on your computer (PC and Mac are both natively supported), and then installing the Eye-Fi Manager software that’s preloaded on the card. (Of course, the versions of the software on my card were older than the current versions available on the company’s website, but the software was smart enough to update itself without any hassle.) From there, the Eye-Fi Manager software launched a clever web-based configuration utility that had me select my wireless network and then select whichever of the supported online services I wanted to use. All in all, it took under five minutes to have the card ready to use.
Since the Eye-Fi is an SD card, I anticipated that I’d have one issue with it up front: our preferred digital camera, the Canon Digital Rebel XT, uses CompactFlash cards. I had read online that CompactFlash-to-SD adapters work fine with the Eye-Fi, though, so this was an easily-surmountable issue. After plugging the card in, our camera wanted me to format the card before it would write photos to it — but the Eye-Fi doesn’t mind being formatted at all, so this too wasn’t really an issue so much as an additional step I needed to take before being able to take pictures. Finally, the folks at Eye-Fi recommend making a change to your camera’s auto-power-off settings — because after all, the card draws power from your camera, and if your camera goes to sleep pretty quickly after you shoot a photo, the card won’t have the power it needs to wirelessly send your photos into the ether. The instructions for our camera weren’t on the Eye-Fi site, but finding the right setting was pretty easy, and under ten minutes from opening the box, my first photo was uploaded and available to me on Flickr. (Note that I set the Eye-Fi to upload all its photos to Flickr as private images, an available feature that I think is pretty much mandatory for a device that automatically uploads every image I take!)
Overall, my assessment of the Eye-Fi is that it’s an amazing and groundbreaking product that belongs in the arsenal of anyone who takes more than a handful of digital photos a week. And for people like us — people who frequently let dozens of photos sit on the camera’s memory card because we’re slightly too busy or lazy to find the card adapter, plug it into our computers, and do the dance of uploading the images online — this thing is a total dream. I’m impressed with the entire user experience, from the packaging to the setup to the nearly invisible functionality (and for those who know me well, you’ll know how rare it is for me to have nothing to fault in the user experience of a new gadget!).
OK, it’s now been about a week since my first installation of Mac OS X 10.5 (aka Leopard), and after the first round of notes, I have a few other observations to throw out there.
- I get the distinct feeling that my MacBook Pro’s battery life is a bit shorter under Leopard than it was under Tiger — there are a bunch of posts to various Mac-related websites saying the same thing, so there appears to be power in numbers here, and not just a funny feeling on my part. That sucks; over the next few weeks, I’ll get the sense of whether it’s a real issue or not.
- The new version of Mail.app seems to have some sort of seriously screwed-up issue with my IMAP account configuration. Last night, my MacBook Pro sounded like an airline tooling up to take off, and I discovered that Mail.app was re-downloading nearly 3 Gb of mail that it already had in its cache, for reasons that I can’t even begin to fathom. Right now, I’m sitting here five minutes after I asked Mail.app to quit, and can still see four processes in the program’s Activity window that don’t seem to want to give way; clicking the stop icon on one of them just led to a spinning rainbow beach ball of doom, and I’ll have to force-quit the app entirely. All in all, a functioning Mail.app is a must-have for me, and if I can’t figure this one out, it’ll mean either moving to another mail application entirely, or downgrading to Tiger.
- Speaking of unstable, I’ve now had to force-quit Finder itself a half-dozen times under Leopard. The first two times, I connected to shared drives, and then noticed that the drives didn’t appear in the “Shared” section of Finder’s sidebar, despite me clearly being connected to them; that meant that in order to disconnect from the shares, I had to manually issue the unmount commands from the terminal prompt. Force-quitting Finder restored their listings in the sidebar, and all related functionality. Then, I noticed that one time, I created a new Spotlight search template and checked the box to have it saved to the sidebar but it didn’t show up; again, force-quitting the Finder fixed the issue. Both of these issues have recurred a few more times, which is pretty annoying. And notably, all the other functionality of the Finder has remained intact during these periods — it’s not like I needed to force-quit the Finder to restore all functionality, just the “Shared” and “Search For” lists in the sidebar.
- And speaking of Spotlight, Leopard’s new implementation might be better in a lot of ways, but it’s pretty broken in a bunch of others. The biggest problem I’ve run into is that Leopard’s Spotlight seems to operate with a bunch of internal, undocumented filters in place that hide whole classes of potential search results, something that others have also noticed. As an example, if you use the basic Spotlight search interface to look for a file that lives in any of the system-type directories (e.g., the system-wide or user-specific Preferences folders), you won’t find the file — those are now excluded from the general search results. The only way to actually get Spotlight to show them to you is to use the advanced interface, enable the “System Files” choice in the criteria drop-down, and set it to “include” — and this setting only applies to your current search. You can create a template for this that you can then access for future searches, but you can’t ever access that template through the basic, upper-right-hand-of-your-screen search interface; instead, it’s a two-step process where you have to manually start your search from the template and then choose it (rather than “This Mac”) from the “Search:” options that are displayed at the top of your search result pane. This is just inane.
- Finally, Leopard lost all knowledge of the printers that I had set up on all my machines… and given that all three machines are in a work environment with multiple printers and setups, this was quite a pain in the ass.
A few notes after upgrading to MacOS X 10.5:
- I installed 10.5 via a standard upgrade, and pretty much everything just worked — all my apps were fine, and one of the only things I had to re-install was a custom certificate in my Java keychain (certainly not a mainstream thing that most others would experience).
- Like most others, I abhor the new way that the Dock shows folders. I’m not sure which of the handful of changes is worse, though; between the idiotic popup fans and the way that a folder is displayed as a stack of the icons of its contents, the whole implementation is broken.
- While the new Terminal app is way better than its Tiger predecessor, it still doesn’t know how to handle fonts. For example, my favorite monospaced programming font, DejaVu Sans Mono, looks nigh unusable in Terminal. And without the ability to set keyboard shortcuts which launch connections to remote servers, iTerm still beats Terminal’s pants off.
- The other major thing I had to reinstall was my Cisco VPN client — but the version I was running under 10.4 still works just fine (as does the fab Shimo app which makes the VPN client usable).
- I’m not wild about the way that Finder windows now look just like iTunes, and it makes me realize how little I care for the new iTunes interface (and thus, the new Finder interface).
- Spaces is also pretty broken (like the inability to wrap around to the beginning of a row or column), so I can’t see it getting much use on my computer. That being said, if they fix it, it’ll probably be an amazing tool for someone like me who has a few distinct workspaces open at any point in time (e.g., my programming apps, my clinical apps, and my general communications apps).
- Screen Sharing is plainly awesome — it finally gives users the same capabilities that Microsoft’s Remote Desktop has given to Windows users for years. (And one unexpected surprise I discovered: bringing up the Finder’s “Connect to Server” window and typing in a “vnc://hostname/” URL does the right thing, launching Screen Sharing and starting up a remote session.) The client app does nice dynamic resizing of the remote desktop, and seems to deal nicely with the typical lagginess of VNC sessions… whatever Apple did, me likey likey.
- The new version of Mail.app doesn’t like MsgFiler, my favorite app for quickly filing messages, and it was disabled the first time Mail.app launched. Fortunately, Adam already has instructions online for getting it back working, and the instructions work perfectly (as does MsgFiler).
- I haven’t used it enough to be sure, but the wireless subsystem seems to pick up networks that are in your “Preferred Networks” list much faster than Tiger did; there were times with Tiger when I’d wait 30-60 seconds for my MacBook Pro to recognize that I was in the presence of one of my known networks, but I feel like I haven’t had to wait more than 10 seconds or so with Leopard.
- While I’m on networking, the new interface for controlling network configurations is just a billion times better than Tiger’s. I can’t put my finger on the exact reasons why, but after using it a few times, it feels like Apple finally got it right.
- Finally, while not Apple’s issue, I’m out on a limb on Leopard since my favorite backup app, SuperDuper, isn’t yet compatible with the new OS version. On my Mac Pros, this isn’t a huge issue since one of them is centrally backed up and the other has a big drive dedicated to Time Machine; on my MacBook Pro, I’m anxiously awaiting the new version of SuperDuper.
That’s all I have for now; this morning, I installed Leopard on the third of the three Macs I use in my regular, day-to-day work, so I’m now immersed enough that I should have a few more observations over the coming days to weeks.
The New York Times ran an awesome article last week about how Big Papi (more formally known as David Ortiz, the designated hitter for the Boston Red Sox) spends most of his time during games reviewing every pitch of the opposing pitcher, as well as all his at bats against the pitcher (from the game in progress and every other game in which they’ve faced each other). Far from the hulking bear that he appears to be, Ortiz is apparently a total nerd when it comes to using technology to improve his batting — unsurprising, since I’ve actually had the chance to meet Big Papi twice, and both times he displayed a knack for being the exact opposite of every stereotype you could possibly muster about him. I think it’s safe to say that while I’m a Yankees fan through and through, I’m also a pretty huge David Ortiz fan, and the fact that he spends his between-bats time shuttling through a video-on-demand system makes me like him even more. (via Jason)
Fascinating: one worthwhile way to speed up your Windows PC’s boot time, according to Jeff Atwood (whose advice I usually find worthwhile), is to disable any antivirus software. Unless you (a) are incredibly secure in your network’s ability to detect and thwart malware and spyware, (b) are 100% secure that there aren’t any undiscovered vulnerabilities in Windows — and in the software you run on your Windows machine — that would allow code to run without your explicit permission, I’d say that that’s pretty solidly some bad advice there.
Ah, the iPhoners now get to see what the difference is between a product Apple controls in every way and a product for which it relies on AT&T to provide some level of service. I can’t fathom why a company with as reasonably great a record as Apple wanted to jump into bed with a company as awful as AT&T… it’s just weird.
Update: Gizmodo gets on the bandwagon and describes the amazingly wide gap between the iPhone-buying experience at an AT&T store and at an Apple store. Guess which store’s staff sucked awfully, treated customers like intruders, and did everything to not give information or assistance to the people who wanted to give them money?
Seriously, I’ve been killing myself trying to figure out why the speakers on my Mac Mini at the office have been popping and crackling at me for the past few days; alas, it looks like my upgrade to OS X 10.4.10 is to blame. What could they have possibly changed in the OS to cause this? It’s one of the odder bugs related to a system upgrade I’ve ever experienced…
Update (7/3/2007): it looks like Apple has fixed the bug; go grab Audio Update 2007-001.
I generally like his writing and his viewpoints, but I can’t help but wonder whether John Gruber’s missive against the enterprise’s wariness about iPhones is based more in his overt Apple lurve or in a lack of understanding of the things an enterprise has to manage on the wireless front. Far from his laser-like focus on email, when a large business thinks about services that need to be extended seamlessly to wireless devices, useful email access shares equal space with the ability to use a global address book, the need to access services on an intranet, ties into enterprise calendaring services, centrally-managed security policies, encryption (both of the contents of the device and communications between the device and other services), and the ability for the enterprise to control access on a device-by-device basis. And again, despite Gruber pointing out that some of the email issues can be solved using IMAP, there are few or no ways to solve the other issues, especially not in as unified a way as BlackBerry has done with the BlackBerry Enterprise Server (BES).
Let’s look at a few example issues, and think of how the iPhone would compare to what BlackBerry has in place.
1. A wireless user needs to be able to send an email to a few enterprise users, none of which are in his contact list. How does that user do this?
BlackBerry: in the email app, the user creates a new email, and in the “To:” line, types in the name of the recipient and chooses the “Lookup” option. The BlackBerry queries the global address list, returns a list of matches, and the user chooses the correct one, which is then added to the recipient list.
iPhone: according to articles like this, the iPhone doesn’t understand global address lists to the point where a developer had to write a raw LDAP client for the device (which we have to assume is a web-based app, given that there’s no native API for the iPhone). So the user has to open Safari, navigate to the web page which provides an LDAP lookup of the global address list, look up the user, and either click a mailto: link to start a new email to the user or cut-and-paste the address into the email client. (And while mailto: certainly is easier, it won’t work for multiple addressees without a really slick web app that allows multiple lookups to all be appended to a single link which will then launch the email app and start a new message. And none of this takes into account the fact that a company will have to write the LDAP lookup app in the first place.)
2. A wireless user needs access to an online database that only exists on a company’s intranet. How does the user get to it?
BlackBerry: given that the BES provides web connectivity that can be routed through the intranet, the user only has to open the BlackBerry Browser application and enter the URL, and will be taken to the web page hosting the database.
iPhone: there’s no similar way for iPhone users to route their web requests through an intranet server; iPhones get their connectivity to the internet through Cingular, and as such, are outside the enterprise firewall, meaning that they can’t get to intranet-only web applications. There’s no info on whether Safari on the iPhone will support the use of web proxies, but even then, use of the proxy will have to be open to the entire Cingular network, opening up a whole other host of security questions and problems. So to achieve this challenge, a company has to either (a) choose to host the web app on a server accessible to the internet at large and implement web-based authentication, (b) implement a public-facing webserver which has authentication and proxies requests for the application to the intranet server, or (c) set up an HTTP proxy server facing the internet and figure out how to secure it such that only authorized iPhone users can get access.
3. A company mandates that all wireless devices need to encrypt all information they store in memory, need to auto-lock after 15 minutes, and need to auto-erase the contents of the device after a given number of incorrect password attempts. In addition, the company wants to be able to wipe a device remotely that’s reported as lost.
BlackBerry: the system administrators create a new security policy with those three rules, push the policy out to all the BlackBerry devices registered on the BES, and then restrict access to the network to only those devices which have the new policy in place. All the devices receive the new policy and implement it; any devices which have more lax security settings are barred from accessing the enterprise. When a user reports their BlackBerry as lost, the sysadmins push a command to the device to wipe its memory.
iPhone: the system administrators recognize that (as of current information) there’s no way to encrypt all the information on the device, and no way to force the device to initialize itself after a given number of incorrect password attempts, so they give up on those two. They then send an email to all known iPhone users pleading with them to set their auto-lock times appropriately, and they hope that the users read the email and follow the directions. And given that it’s unclear whether there are any mechanisms of access control for specific iPhones, they continue to hope that the rules are being followed. As for lost iPhones giving up their data, there’s nothing that would allow for remote erasing, so the company also hopes that there’s nothing sensitive on the device.
4. Finally, given that I’m a physician, something that’s relevant to my world: an organization exists in a world which mandates that all electronic communications about patient care are encrypted from end to end, and system administrators are tasked with making sure their wireless devices comply with this requirement.
BlackBerry: the system administrators install the S/MIME add-on and the enterprise security certificate chain on all enterprise BlackBerries. They then have the users install their personal secure email certificate in their chains, as well, and then users can query the enterprise directory for other users’ secure certs and can choose encryption as an option on the email composition screen.
iPhone: from the bits of news coverage and reviews I’ve found, there doesn’t seem to be any encrypted email support on the iPhone, so there’s nothing the organization can do. It’s unclear whether the phone’s mail client can require — or even support — users’ connections to an IMAP server over SSL, so in addition to the actual email, the communications channel over which that email travels might be totally unencrypted.
There are oodles more issues that could be brought up, but the gist of the matter is that no matter how much people in the enterprise crave being able to replace their BlackBerries with iPhones, the support for the devices working at the enterprise level isn’t there. And given Apple’s pretty awful track record when it comes to integrating their other products into the corporate environment, you’d be naive to think that a seamless iPhone experience in the enterprise is coming anytime soon.
In the past 48 hours, I’ve had two very weird issues pop up on my MacBook Pro, issues that are so weird as to make me wonder what gremlin has made its way into the innards of my laptop.
First, two days ago, I noticed that anytime a string was displayed in a bold font, letters were dropped out of the string. Initially, I saw it happening on web pages in Firefox, and figured it was a bug in the app, but opening up Safari I saw the same exact issue. Then, I checked to see if Mail.app was doing the same thing, and sure enough, there were dropped letters aplenty in the bold strings of HTML emails. Same thing in every other app I tested, and there was nothing running that could explain the weirdness. Rebooting the machine solved the issue.
Then, tonight, I noticed that I wasn’t hearing the “whoosh” of sent email in Mail.app, nor was I hearing the new mail alert. Entourage was still making its noises, though, but Adium wasn’t; the Sound preference pane wasn’t playing samples of the sounds as I chose them as the default alert. Again, there was nothing running that would have caused the weirdness, and it persisted even when I quit all applications — and again, rebooting the machine solved the issue.
I thought that the era of rebooting your Mac every so often to keep things running right was long past, but might it be making a comeback?
A few short takes:
- Michael Lopp, the man behind the weblog Rands in Repose, has the computer monitor setup I can only dream about. That’s a 30-inch Cinema Display on the left, and a 20-inch Cinema Display — turned vertically — on the right… all I can say is wow. Maybe if I lead a good, clean life from here on out…
- I’m generally not the largest fan of Walt Mossberg’s, but he’s dead-on in his evaluation of today’s typical first-run experience on new Windows PCs. It literally takes hours to wade through all the crapware that manufacturers load onto a new PC these days, getting rid of trialware and all the other useless dreck that comes along for the ride; it’s one of the biggest differences between the first-run experiences on PCs and on Macs.
- Mostly as a bookmark for myself: here’s how you tell your Mac to stop creating the annoying .DS_Store files on Windows file shares. Damn, these are one of the more irritating things that come part and parcel with using Macs in a Windows networked environment…
- ImgRed.com, a new “service” that claims to provide a good cache for images you’d like to link to on the web, has collected a good number of links over the past few days; I’d love to know what their privacy policy is, though, and how the service plans to give webmasters the ability to prevent caching of images on a given site (since it’s fundamentally a whopping copyright violation in the making).
When home users back up their computers, a lot don’t think about the fact that in some scenarios of data loss, those backups won’t do them any good — the scenarios which involve the loss of both their computer and their backups. (Think home fire, or burglary that involves taking the computer and the external hard disk that contains the backup.) For this reason, one tenet of most corporations’ backup plans is that an entire backup set exists off-site from the machines that are being backed up — safety through separation. There are hundreds of thousands of corporations who have the need to manage this process, so as a result, there’s a market of off-site storage providers that’s expanded and matured in a way that supports the importance of the data that’s being moved into storage. The big players have service agreements that stipulate the time frame in which customers can get their data, they provide reasonable guarantees for the safety of the data, and they put quite a bit of effort into meeting these guarantees.
In today’s day and age, home users are installing internet connections with more and more bandwidth, and this has opened up the potential that these users can actually back up their computers to some off-site location over the internet; unsurprisingly, a group of services has popped up to support this potential, services like .Mac, AT&T Online Vault, Mozy, and Carbonite, and even applications like JungleDisk and Amazon S3 which provide the infrastructure to allow users to take a more customized or do-it-yourself approach to online backups. As we’re talking about backups of people’s data, you’d think that these services would provide similar guarantees about the data’s availability and the services’ reliability, yes? Alas, that appears to be a false assumption. Ed Foster, everyone’s favorite griper, took a look at the end-user license agreements for a few of the online backup services back in mid-February, and he was pretty amazed to find that all the ones he investigated disclaimed pretty much any responsibility for the usability or availability of the backups, or even for the functionality of the services at all. (Granted, at least a few of the services he examined were provided for free — so in the end, you get what you pay for — but others are paid services.) That’s a real shame… but I’d imagine that it’s also an indication that there’s a real market niche waiting for the right company to come in and provide the right level of service.
For all of you who are using the occasion of Window Vista’s release to rekindle old Mac-vs-PC flames, I suggest you take a little time to read Jeff Atwood’s post from yesterday. I don’t think I can agree with him strongly enough; while I live my life surrounded by computers (literally — a half-dozen in the home, a research career centered around them, a few hobbies dependent on them), they certainly are enormous pains in the ass half the time.
Take this weekend, when I found myself in the basement at my workbench and needed to look something up on the web. My old laptop — a Powerbook G4 I haven’t used in a few months — was sitting on top of the workbench, so I opened it up and launched Firefox. The first thing I was greeted with was “Firefox is now installing all your updates”; that process ended up taking nearly three minutes to complete. During this, I launched Safari, but as I was typing in the address bar, a window popped up alerting me to a slew of operating system updates waiting to be downloaded and installed. I ignored that, searched for and found the tool manual I was looking for, and clicked on the link to the PDF, after which I was greeted with a warning from Acrobat Reader telling me that the file had features that were too new to be supported in that version of the application. It was five or ten minutes of sheer frustration, all in the name of finding a freaking piece of information on the web.
Jeff is right on when he says that these days, the best electronic devices out there are special-purpose ones that do a small handful of things incredibly well; the more functionality and geegaws a manufacturer adds to a device, the less stable, reliable, and usable that device will be. And when push comes to shove, all these devices are just tools, and they matter far, far less than what we do with them. In Jeff’s words:
That’s the other problem with the Mac vs. PC debate: it completely misses the point. Computers aren’t couture, they’re screwdrivers. Your screwdriver rocks, and our screwdriver sucks. So what? They’re screwdrivers. If you really want to convince us, stop talking about your screwdriver, and show us what you’ve created with it.
In the department of giving credit where credit is due, I have to say that I had occasion today to use Dell’s online manuals for the disassembly and servicing of the company’s laptops, and I was extremely impressed.
At the end of last week, the laptop of a family member of mine had an unfortunate run-in with a nearly-full cup of Dunkin Donuts coffee, and amazingly, the keyboard bore 100% of the brunt of the unprovoked attack. He quickly shut the machine down and dried off the keyboard as best as he could, and then tried to take the worst-hit regions of the keyboard apart to dry the membrane underneath. Alas, as is the case with most laptop keyboards, that was a road fraught with peril, and the result was one broken spacebar, a few misaligned key caps, and a bunch of keys that just didn’t work anymore. He enlisted my help, and we found that a replacement keyboard from Dell cost a very reasonable $25, so we ordered it up. The part came yesterday, and the service manual gave very clear directions on all the steps needed to get the broken keyboard out and replace it with the new one. In fact, they were so clear that I also felt confident enough to remove the display and the entire top section of the laptop’s plastic case, fix an older problem with the trackpad’s buttons, and put the whole thing back together again. (And there weren’t any stray screws left over at the end!)
I know that Dell has had its share of issues over the years, but in this case, the presence of accessible and well-illustrated service manuals made me pretty happy.
For those of you who are salivating over Apple’s newly-announced iPhone, you might want to do a little research on Cingular, the other company you’ll be getting into bed with if you run out and get an iPhone in June. As an example, did you know that Cingular now forces you to waive all rights to trials by jury or participation in class-action lawsuits in order to become customers of its services? Or that its number of complaints per million customers is nearly double that of the next large market player (T-Mobile)?
In all honesty, the most amazing thing to me about Apple’s iPhone announcement is the exclusive multi-year pairing with Cingular, which locks Apple fans into an agreement with what might be one of the most customer-hostile companies ever. And what’s worse, can you imagine how awful it will be if the expectation is that customers go to Cingular for all techinical support of the iPhone?
I guess this’ll all play out in the coming months, but my first reaction to the whole thing is that this might be the time that Apple learns what it’s like to release what looks by all accounts to be an amazing device into a world in which the company doesn’t exert 90-plus percent control of the entire end-to-end user experience. Hopefully, it’s planning on some clever strategies to deal with this… but I can’t see the Cingular side of this going well at all.
Lately, a little bit of press has been given to people who claim to be sensitive to wireless network or cellphone signals, some of whom have convinced school systems to remove wireless networking from entire buildings in order to protect themselves and their children. This has always been a little fishy to me (I posted about an Oak Park, Illinois debate back in October of 2003); these signals are pretty much omnipresent at this point (for example, microwaves put out quite a bit of energy at the same frequency as WiFi), so getting rid of a single WiFi access point or cellphone isn’t really making that big a dent in the total sum of non-ionizing radiation that surrounds any one person. Well, thankfully, there’s now some science to support that position: the British Medical Journal performed a double-blinded, randomized, placebo-controlled study and found that those who claimed to be sensitive to GSM cellphones were unable to identify the presence or absence of a phone with any reliability. Better still, when individuals with ostensible symptoms of sensitivity were told that the wireless signal had been discontinued, their symptoms improved whether or not a signal had been discontinued. The same study hasn’t been done with WiFi yet, but it’s just a matter of time. (Thanks to Glenn for the pointer.)
While adding a bunch of scheduled meetings to my 2007 calendar today, I came across a fascinating little bug in Microsoft Entourage, a bug that’s related to the US decision to shift around a bit the start and end of Daylight Savings Time. (The move was part of the Energy Policy Act of 2005, and is ostensibly temporary until the government can study the changes and determine if they truly do result in energy savings.) Because Entourage predates the DST changes by quite a bit, it gets confused between March 11th and March 31st of 2007, and between October 29th and November 4th of 2007 — the former is because the start of DST was shifted back from April 1st to March 11th, and the latter is because the end of DST was shifted forward from October 29th to November 5th. The result of the bug is that the calendar shows all event times as an hour later than those which were entered (for example, a start time of 8:30 AM in the event detail dialog box shows up as 9:30 AM on the calendar).
I’m sure that Microsoft will get around to fixing this sometime before mid-March of 2007, but until then, be aware of the bug when you’re scheduling events with Entourage!
At around 11:00 PM last night, my three week-old MacBook Pro Core 2 Duo laptop had a kernel panic, and afterwards, it wouldn’t reboot. I tried to use Disk Utility (from the installation DVD) to repair the hard disk, but it errored out (saying that the hard disk couldn’t be unmounted); the same error occurred when I put the machine into target disk mode and mounted it on my old 12” Powerbook. I was able to boot the MacBook Pro into single-user mode and try to use fsck to diagnose the disk, but it too threw an error (0xe0030005 UNDEFINED, Invalid node structure) and refused to complete. Thinking about third-party hard disk diagnosis and repair tools, I quickly learned that DiskWarrior doesn’t run on the Intel Macs yet, and TechTool doesn’t run on the MacBook Pro Core 2 Duos yet (not that I have it, being that AppleCare takes three to four weeks to process applications and provide the software to users). At around 3 AM, I realized that I could get at around 80-90% of my files using single-user mode, mount a USB hard disk, and use rsync to copy the still-accessible files over to the drive, a process that took enough patience and debugging that it didn’t complete until around 5 PM today.
Needless to say, I’m frustrated, a frustration that’s amplified tenfold by the fact that I’m traveling this Friday evening, and really really wanted to have my laptop with me for the five-day trip. I’m fortunate to work for a huge federal agency that has an on-site support and repair contract with Apple, but it’s unclear that they’re going to be able to get me back up and running by the time I leave town.
Sometimes, technology sucks.
Ever since moving my life onto a Mac laptop, I’ve been using Apple’s Mail.app as my primary email application. In general, it’s a great program, but for someone like me who has a lot of email folders, it’s a bit irritating using its interface to move messages around — there’s a lot of scrolling of the folder sidebar involved, and no good way to shortcut that process. (Plug-ins like Mail Act-On get part of the way there, but are too specific to solve the more general problem.) Imagine my happiness, then, when I saw Adam Tow’s MsgFiler come across VersionTracker this afternoon… it’s the Mail.app plugin I’ve been dying for someone to write! Within two or three minutes of installing it, I paid the shareware fee and dropped Adam a note expressing my undying gratitude; if you’re as annoyed by Mail.app’s folder handling, I might recommend you do the same.
Update: Wow, that’s weird — two people who impress me on nearly a daily basis, Alex King and John Gruber, both feel the same way about MsgFiler!
In terms of laptops, I’m pretty solidly in the Apple crowd, having had a 12” Powerbook G4 for the past two-plus years and now having upgraded to a MacBook Pro last week. Since I moved to DC and become a member of the CrackBerry crowd, I’ve salivated over the idea that someone might figure out how to let me tether my BlackBerry to my Mac and allow me to use the data connection to access the ‘net (something that RIM supports out-of-the-box for PC users), and was pretty excited when Alex King offered a bounty for the feature and things started moving a bit. A month ago, Daniel Pasco claimed the bounty with Pulse, a product he’s developing that aims to use a Bluetooth connection to let you connect to your BlackBerry, and with my desire to see this working I’ve been following the app’s development closely. Today, Daniel posted an update with some incredibly interesting — and disappointing — information: the Bluetooth implementations are wildly different across the various BlackBerry models, with the Pulse able to sustain data rates that are more than five times faster than those the 8700g (my model) is able to pull off, and the 8700g’s rates are two times faster than the 7290. That’s really pretty amazing… in chatting with Daniel, he’s only 95% sure that this isn’t some weirdness in his testing setup, and he’s holding out hope that someone might be able to weigh in on what might be going on here.
If you’re knowledgeable in the Mysterious Ways of the BlackBerry Bluetooth Stack and have something that might point Daniel in the right direction, I’m sure he’d be thrilled if you’d go leave him a comment!
There are times when I think I’m finally reaching a reasonable level of coolness, and then there are times I see something like Sun’s datacenter in a shipping container, feel myself start to drool, and realize that I’m still the huge geek I’ve always been.
An online article that’s making the rounds right now is Aalaap Ghag’s “Guide to Useless Services”, which purports to be a list of the services running under Windows XP that exist only to slow you down (and thus can be shut off without a problem). After giving it a read, though, it seems that Mr. Ghag doesn’t have the slightest clue about the subject, and I’d honestly hate to be in the position of supporting any computer that has the misfortune of having his advice applied to it. Let’s demonstrate with a few examples.
His first entry, for the Computer Browser service, reads as follows: “Contrary to what it may sound like, disabling this service still allows you to browse a network in your office. And of course, you don’t need this at home. Disable it.” Alas, if you (like many homes these days) have more than one computer and expect to be able to share files or printers across them, then you’re screwing yourself; the Browser service is what allows you to use your Network Neighborhood by maintaining the master list of shareable resources on a network and letting computers find those resources. In fact, when he says “disabling this service still allows you to browse a network in your office,” this is only because another computer somewhere in the office is successfully running the Browser service.
Now, onto the Error Reporting Service, which Mr. Ghag addresses as such: “I.e. ‘Send system information to Microsoft.’ No thanks. Disable it.” Sure, that’s a great idea, if you want to cut off your nose to spite your face. When an application crashes under Windows, the ERS allows your computer to send information about the crash back to Microsoft, both to collect data about what caused it and to see if there’s a fix for it. (For example, if a display driver causes a crash, and the manufacturer has released a version that specifically fixes the bug, then you’ll get a link to download the new driver.) This has helped me immensely on more than one occasion, and in any event, if you’ve ever bitched about MS having buggy software, then you shouldn’t turn around and cut off one avenue the company has opened towards eradicating those bugs.
As for the Indexing Service, the advice given is: “Use AvaFind and/or Google Desktop Search instead. Just disable it - no questions asked.” Huh?!? The Indexing Service does a great job of setting your computer up for much easier file searches from right there within the operating system; saying that people should shut it off and use third-party apps doesn’t make any sense to me.
Finally, the kicker is this gem about the System Restore Service: “I prefer trying to manually troubleshoot and fix, or reinstalling Windows in case of a fatal problem. I’ve never felt comfortable with using System Restore to ‘restore old versions of files’ and all that, so I keep it disabled. It frees up memory and a good amount of disk space as well.” Literally, this is like saying, “When I have a flat tire, I prefer to lift my car off the roadway with a series of rocks found in the bushes, and then fashion a new tire by felling a nearby tree and whittling it down to size. It frees up all that space in my trunk that a spare and jack would have taken up!” The System Restore Service is honestly one of the best ways to back out of a system change that’s left you totally horked, and in my experience, the only good that can come out of disabling it is that you’ll become a lot more familiar with the whole system reinstallation process.
I guess my perspective is that if you know enough about how each of these services works, sure, there are probably a million scenarios for where shutting a handful of them off might serve a given user well. But don’t mistake this article for adequate information about any of them, and certainly don’t follow its advice unless you either know what you’re doing or don’t care if your computer becomes significantly less functional.
Wowzers, I had no idea that Amazon is offering a $100 rebate on the new Apple MacBooks (that’s the 2.0 GHz model, but the same rebate’s available on the 1.83 GHz one, and on the black MacBook). That puts ‘em at the same price as is available under an educational discount, which is pretty amazing. I’ve started to hear good things about the MacBooks from a few people I trust who grabbed them as soon as they came out; it makes me think that as soon as I’m no longer able to tolerate my 12” PowerBook, I might know what my next machine wil be…
Wow, do the folks at Microsoft have some balls. My Windows XP desktop box alerted me about a high-priority system update today, an update which turned out to be a new version of the Windows Genuine Advantage Validation Tool. I’ve been asked to install updates to the tool a few times in the past, but this was the first time I’ve also been asked to read and consent to an end-user license agreement. I guess I was teased by the novelty of a license for Microsoft’s anti-piracy tool, so I read a little bit of it, and noticed that it prominently proclaims to be is pre-release software. What the f*@%?
It turns out I’m not the first person to notice this — over at InfoWorld, Ed Foster picked it up and turned it into a Gripe Line post last week, and found a lot of other problems with the license as well, including a ban on users uninstalling the software, and a clear statement saying that Microsoft will not provide any support for the software. Looking at the Microsoft Knowledge Base article about the update, there’s no mention of it being pre-release software, and the Windows Update installer never notifies users (in a way other than buried in a EULA) that this is an optional installation of less-than-adequately tested software for which users will receive no support and no uninstallation capabilities in the case of problems. I find this all — the pushing of pre-release software out as a high-priority Windows Update, and the inclusion of terms in that software which make it hard to stomach — pretty odd and incredibly sleazy.
Sorry about the complete silence from the Land of Cheese lately — Real Life™ intervened (a dying patient, a push to secure my post-fellowship future, a semi-urgent need to upgrade the lifeblood of the Queso network, and a baffling attempt to understand the world of home financing). Things are slowly returning to normal, though, and I hope to be as chatty as ever soon!
In the mean time, I have to say that one recommendation I got over the past week that’s served me incredibly well is Matt telling me to give reBlog a shot. It’s a website syndication aggregator, built on the codebase of one of my favorite (but increasingly neglected) apps, and it’s just frickin’ amazing. (Matt authored a review, complete with a screencast, over at Lifehacker today.) Because of the aforementioned system upgrade, I actually uncovered a wee little bug in reBlog, but the code was easy enough to read that I banged out a fix for it over the course of a night and I’m now pretty much sold on the app. If you’re in the market for a web-based aggregator, go set up an account on the online demo app and see what you think.
For the second time in just under three months, I turned on my iPod today and was greeted with the sad iPod graphic. Once again, I found myself at the Apple Store, where it was quickly determined that the hard disk in my replacement iPod had failed exactly as the first one had. Once again, my iPod was whisked away and replaced with a refurbished one. And once again, as I sat there syncing all my music to the new iPod, I watched as nearly a dozen people came through and had their iPods replaced in the exact same way mine was, all before noon.
Let’s assume that my local Apple Store replaced somewhere on the order of two dozen iPods today, that the customers at my store aren’t any different than those anywhere else, and that today wasn’t any different than any other day. Given that there are 126 Apple Stores in the United States, this would mean that Apple replaces roughly three thousand iPods a day, twenty thousand each week, and over a million a year. Could these numbers possibly be correct?
Interesting — while I certainly had a good experience with my iPod replacement over the weekend, it turns out that the iPod warranty would have allowed Apple to charge me $30 to get me back in business, ostensibly for “shipping and handling.” (Note that the Genius didn’t attempt to charge me, nor did he attempt to charge any of the other people who replaced their iPods while I was in the store.) I agree with the person who mailed the info into Macintouch — the notion of a warranty that adds some sort of service charge halfway through the warranty term feels dirty, and certainly makes the warranty a lot less valuable. Also, the charge means that adding an extended warranty to your iPod isn’t $59, it’s actually a minimum of $89 — you have to pay the $59, and then each time you need to send your iPod in for service, you’ll have to pay another $30. Bleah.
(By the way, is this the right place to beg Macintouch’s Ric Ford to create permanent links to entries of his? The link above will only work until the item leaves the front page of Macintouch; then, I’ll have to dig through his search engine and archives to find a link that might continue to work.)
Shannon and I came to Sacramento last night for a wedding reception, and on the plane, my iPod went from happily letting me navigate its menus to sadly showing me a graphic of a frowning iPod and a URL for iPod support. So when we hit our hotel last night, I immediately went online and made an appointment with the Genius Bar at the Apple Store across the street, hoping to at least get the repair process started. Today, I walked in, the guy immediately determined that the hard disk was dead, and offered to replace the iPod on the spot — a decision that was only made difficult by the fact that Shannon had the iPod engraved when she gave it to me as a Christmas/engagement present. (The alternative I was offered was to mail it back into Apple, where they’d fix it and return it to me with the engraving intact.) My desire to have the little guy back in shape ASAP motivated me to choose the on-the-spot replacement, and I’m sitting here at the Genius Bar (using the free Apple Store WiFi) while the new machine syncs up with my Powerbook.
There is one thing that’s more amazing to me than the quick, efficient service I got here, though — it’s the number of other people who’ve sat down beside me, broken iPod in hand, and had their players replaced on-the-spot too. In the last half-hour, the Genius has replaced six different iPods, ordered warrantly replacements for another two, and he tells me that he has a half-dozen other iPod-related appointments on the calendar for the remainder of the day. It makes me pretty happy to see that Apple’s willing to do fast warranty service on a walk-in basis, something that keeps its customers coming back.
In today’s technology section, the New York Times confirms something that I’ve been hearing about from friends and coworkers for about a year now: rather than cleaning their computers of viruses and spyware, people are now throwing the machines away and buying new ones. At first, this struck me as completely odd, since I’d never had any problems using antivirus apps regularly, using spyware cleaning apps as needed, and practicing as safe computing as possible to prevent obvious installations of apps that’d break my machines. But I can’t deny the sense that adware is now embedded in far, far more apps, viruses are exploiting much more subtle holes, and the process of getting rid of unwanted or malicious apps is significantly harder now. (Hell, last weekend, it took me three antispyware runs and five reboots to get a single app off of my parents’ laptop, and I know what I’m doing!) When you add the fact that computer prices are dropping quickly (for example, you can get a fast Dell desktop with a 19” flat-screen LCD for $499 right now, and a more entry-level Dell with a 15” LCD for $299!), I can see why people are tempted to just trash their old machines and start over, even if it means figuring out how to get all their files moved over and set all their peripherals back up.
And worse still, looking at the situation from that perspective, why should computer manufacturers work hard to support their users by helping them remove adware or viruses, if the alternative is to convince them just to buy new machines? Seems like a no-brainer for them, which is all the worse for us end users.
This weekend, I finally got around to helping my brother get some files off of an old Powerbook Duo 230 that he’s been keeping in storage; I was pleasantly surprised that I was even able to get the laptop onto the internet. I’ve put a few photos up on Flickr, just for kicks.
Since I’ve been gone for so long (almost a week!), a few quickies to get ‘em out of the ever-accumulating to-do bookmark list:
- My parents gave Shannon and me our wedding present early — a Canon EOS 350D (also known as the Digital Rebel XT, reviewed here at Rob Galbraith’s awesome Digital Photography Review) — and this thing is just amazing. I’ve played quite a bit with digital SLRs, and this is the best of the prosumer ones I’ve used; the images (even the compressed JPEGs) are bright and crisp, it autofocuses fast even in low light, the shooting modes run the gamut from letting the camera handle everything to manually controlling every last detail, and between the in-camera memory buffer and the CompactFlash write speed, I haven’t yet found myself in a position where the camera prevents me from shooting in order to catch up. Shannon and I had a blast with it during the Fourth of July weekend, and I’ve started tagging all the Flickr photos I’ve shot using the new toy. Fun fun!
- I’m with Jason Kottke on this one — Microsoft’s page explaining leetspeak to parents has to be a joke, or at least the result of a bet made by some Microsoft employee about whether or not he could get the article online without anyone noticing.
- I totally dig these “Charles Darwin has a posse” stickers — they’re cool as hell, and come in a handy PDF version as well!
- After more than a month of inundation with news about another missing American white girl, I’m pretty much on board with the sentiment behind this op-ed over at Kuro5hin. Arianna Huffington also puts it pretty well, and provides some pretty depressing observations on the media coverage of the Aruban Abomination.
Take a look at this dialog box, and tell me the exact steps you’d go through to carry out the choice of contacting APC to upgrade your uninterruptible power supply:
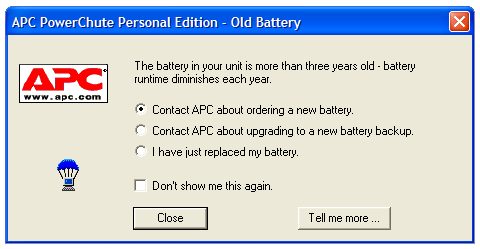
After selecting the radio button, do you click “Close”? Or is it “Tell me more…”? And if you check off “Don’t show me this again” but you choose the wrong button, how can you get this dialog to come back?
A few other irritating things about this dialog box:
- It doesn’t show up in the Windows taskbar, so if you want to put off your decision while you finish other work, you then have to minimize all your other work in order to get back to the dialog box.
- APC doesn’t provide any tool that actually tells you the manufacture date of the battery, but instead wants you to trust that the popup isn’t making an error in date calculation.
- I bought this UPS under two years ago, sometime after I moved to Brookline, so either it sat in the distribution channel for over a year, or the date calculation is wrong.
From the logs of my new uninterruptible power supply monitoring application:
Tue May 03 06:46:02 EDT 2005 Power failure.
Tue May 03 06:46:05 EDT 2005 Power is back. UPS running on mains.
Ahhh, that’s nice to see — last week, this would have brought part of my home setup to a screeching halt.
To flip the coin over from my suboptimal service experience last week, I feel like I should relay the fantastic experience I had this week with PowerBookResQ.
This past weekend, I decided to pull my iBook (the laptop I used before treating myself to a 12” Powerbook last year) out and install all of the available updates, clean off all my old documents, and finally deauthorize it from my iTunes account. I hadn’t used it in over six or eight months, but when I put it into storage, it was running perfectly well, and had only been retired because of my craving for a smaller, more powerful laptop. I turned it on, got through all the OS X updates, and then started hearing a little metallic noise coming from the hard disk. The noise started increasing in frequency, and then about ten minutes after it started, the computer crashed and refused to restart. After a bunch of diagnostic steps, I gave in to the obvious — the hard disk had died, and if I wanted to keep the machine around and usable, I’d have to replace it.
Opening up an iBook to replace a hard disk is notoriously difficult, but I still contemplated it for a while. I decided to see what companies were offering to replace hard disks in the machines online, too, and found the folks at PowerBookResQ. According to their website, they offer a 72-hour turnaround on hard disk replacements, and after a conversation with them, I decided to give it a try. On Tuesday, I called them around 4PM and placed my order for a 60Gb drive, and Wednesday afternoon, a custom laptop shipping box appeared on my doorstep. I put my laptop in, sealed the box, called DHL to arrange the return trip, and by 7PM on Wednesday, DHL had come to take the computer away. Tracking it, I saw that it arrived back at PowerBookResQ yesterday (Thursday) morning, and then when I got back from work today (Friday), it was waiting for me on the landing outside my apartment. That’s a less than 72-hour turnaround, and the machine works perfectly.
While there are plenty of companies that do their job well, it’s rare for me to be totally stunned by the service that I receive. This is one of those times, and I can’t recommend them enough.
I’ve been spending the last few days emergently migrating one of my Linux machines over to a replacement, and tonight, I found myself in need of remembering a command-line option to the utility su. And while looking it up, I discovered a little tract at the bottom of the manual page that left me a bit baffled.
Why GNU `su' does not support the `wheel' group
-----------------------------------------------
(This section is by Richard Stallman.)
Sometimes a few of the users try to hold total power over all the
rest. For example, in 1984, a few users at the MIT AI lab decided to
seize power by changing the operator password on the Twenex system and
keeping it secret from everyone else. (I was able to thwart this coup
and give power back to the users by patching the kernel, but I wouldn't
know how to do that in Unix.)
However, occasionally the rulers do tell someone. Under the usual
`su' mechanism, once someone learns the root password who sympathizes
with the ordinary users, he or she can tell the rest. The "wheel
group" feature would make this impossible, and thus cement the power of
the rulers.
I'm on the side of the masses, not that of the rulers. If you are
used to supporting the bosses and sysadmins in whatever they do, you
might find this idea strange at first.
While I’ve heard that Richard Stallman is just plain crazy, I guess I never understood exactly how crazy. Anyone out there have the root password to his machines?


