Waiting for a flight Thursday evening, I opened up my Powerbook to see if the Gods of Wireless Networking had yet talked some sense into the folks who run Washington’s National Airport. Alas, there weren’t any legit wifi signals available — I specify “legit”, though, because there were quite a few ad-hoc networks set up that looked to be trying to phish and scam their way into information from unsuspecting or naive flyers.
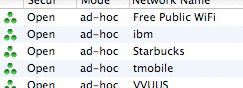
If you look at that list, what you’ll notice is that all of those networks are running in “ad-hoc” (or peer-to-peer) mode, which almost certainly means that rather than them being bona-fide wireless access points serving up connections to the internet, someone’s computer is advertising its own wireless network as available for sharing, and that person is trying to get you to connect to it. That network named “tmobile” is very unlikely to be run by T-Mobile; that network named “Starbucks” is similarly illegitimate. Instead of T-Mobile providing access to the internet, some schmuck is probably trying to entice you to connect your laptop to his, which means that he can then listen in on all your network traffic (sniffing passwords and other data) with relative ease.
Almost without exception, all trustworthy wireless access points run in what’s called “infrastructure” mode. The list of networks in that screenshot is generated by an awesome Mac app named iStumbler, but the built-in networking stuff in any Windows or Mac computer similarly makes a distinction between ad-hoc and infrastructure networks — the Mac separates ad-hoc networks into their own list (“Computer-to-Computer networks”), and if I remember correctly, Windows shows ad-hoc networks with different icons than infrastructure ones. So if you find yourself looking to use wireless access in an airport, make sure you know how to tell the difference between reasonably legitimate networks and scammers; your credit cards, bank accounts, personal files, and email systems will thank you!